
Do we really need resource comsumption settings for cPGuard?
What do you mean by resource consumption?
Every software needs some resources to run on a system and perform its operations. The amount of resources each program need is different and depends on the task it performs. Softwares that need to run multiple algorithms, do complex computations and has a lot of file and network operations are usually highly resource-intensive (specifically CPU, RAM and Disk IO). An anti-virus scanner come under this category as there are a large number of file read writes, content analysis, pattern recognition and comparisons to be performed.
On a server environment resources and limited and required to be available on-demand for the servers primary task. Therefore antivirus scanners have settings to adjust the resources it can consume or schedule the scanner to run in off-peak hours.
So why cPGuard does not allow users to limit it?
We have strictly maintained a “performance-oriented” approach while building cPGuard and wanted it to run smoothly on the smallest of servers. The cPGuard scanner engine core is built to work fast and consume minimal resources. Some of the major points that help us achieve better performance with lower resources are
- We scan only relevant files/locations, unlike the competitors where they scan a lot of unnecessary locations and waste server resources.
- Our core scanner is single-threaded and will not cause a total server spike. So CPU limiting is not required for our scanner daemon
- Our highly efficient and optimised algorithms leave only a very small memory footprint.
- Our IPDB rules contain only active attack sources and thus load only minimal rules and reduce network overhead
- WAF contains only minimal but generic rules which effectively block most and major web attacks
Do you have any proof?
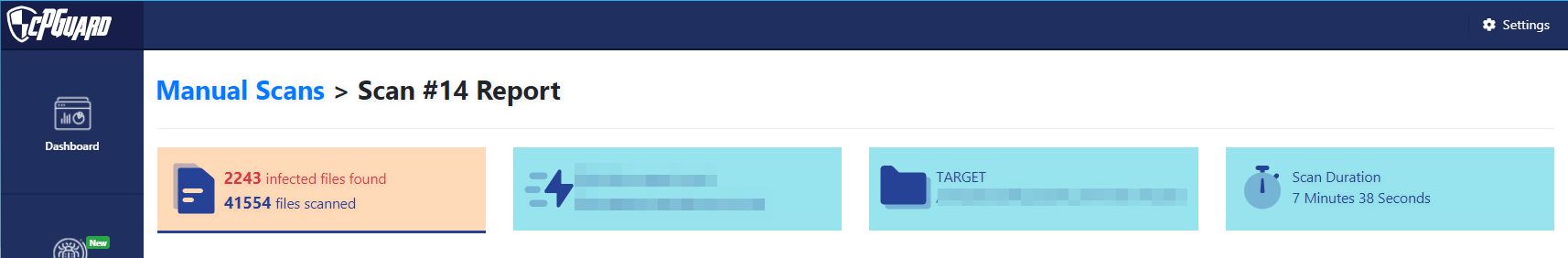
Yes, we have and we can confidently claim our statement. The biggest proof is that in the last 4 years the complaints due to resource usage are close to ZERO. The major portion of most systems that can cause a load spike on the server is the scanner module. Our scanner is fine-tuned to avoid such a scenario and it is one of the fastest scanners available in the market. It is tested and confirmed that the cPGuard scanner engine is more than 7x faster than that of our competitors. The screenshot below of the manual scan option in cPGuard, where it completed scanning 41K+ files in just 7 mins.
So is there any advantage with Resource Consumption settings?
Yes, there is if the scanner module is resource hungry. It will help to reduce server load but it will drastically slow down the scanning process and will engage resources for a longer time. As I stated earlier, that is not a problem with cPGuard and you do not need to worry about setting up such values and monitoring our services.
Ok, I have few more questions…
We are happy to address them…feel free to reach our support team and we will be more than happy to answer your questions!




