We have released cPGuard version 4.58 recently with 2 major features added. We believe the latest features will be helpful for our customers to automatically manage abusive attempts to compromise an account/website and send alerts to the end user and the server administrator. The 2 new features are explained below.
Suspicious User Activity Tracking for cPanel
We have been noticing so many suspicious activities reported, especially on cPanel servers where the hackers could authenticate using valid credentials and do malicious activities on the account. By gaining access to the compromised accounts, the hackers usually upload virus files, backdoors, phishing contents, or completely wipe the website files. The actions are not limited to these but they can do anything they wish to do on the account. This is a widespread compromise and there are thousands of cPanel accounts compromised mostly happened mostly collected through the compromised user’s system and spam campaigns. It is possible that such credentials are being sold on the web for money. In such cases, the only and first fix is to reset the user account password and possibly enable 2FA.
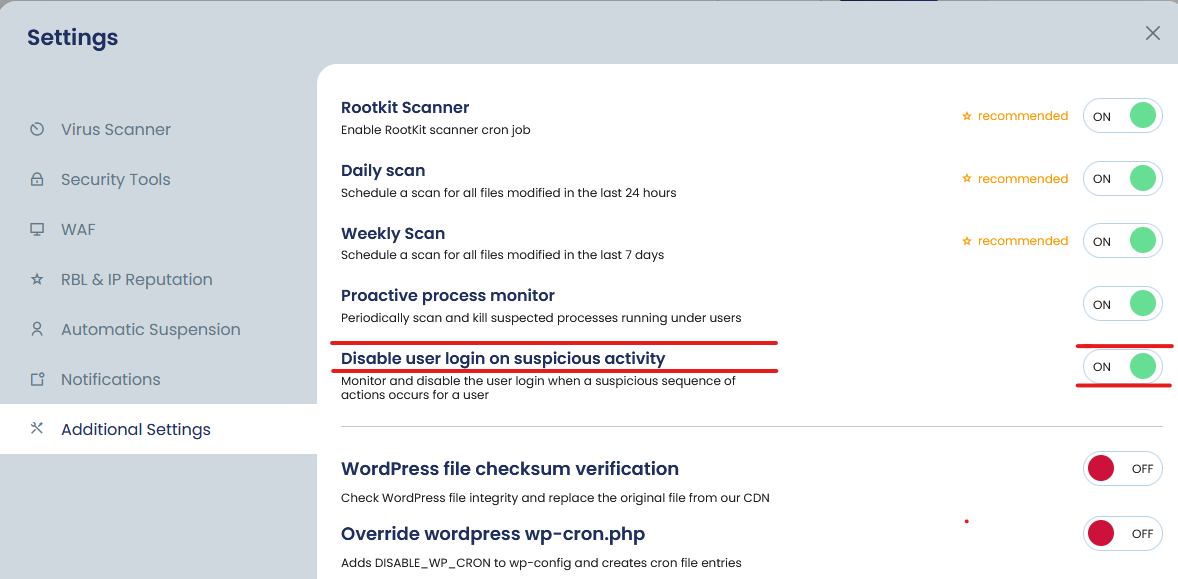
By watching the activities and repeated incidents across some of our customer’s servers, we have added a new option to monitor the user activities after a virus incident is reported under a user. Please note that this new option will not help if the hacker wipes all files, but if they upload bad files and cPGuard can find them, the new logic will trigger. You can enable the new option from cPGuard >> Settings >> Additional Settings. Please note that, this will option will disable all new logins and you need to force reset the user password to restore the login access. Everything else like the websites, emails, etc will work fine.
WordPress file checksum verification and restoration
It is another major issue we have been noticing where some random WordPress core files get bad code injection and thus cause a website malfunction. Many times such injections install malware, a backdoor, or a malicious redirect. Many times the injected code can repeatedly replace the index.php or the .htaccess file with malicious content and that actually disables the actual use of the reported file cleanup. We have been noticing that the injected code patterns are different in many cases and it is very difficult to identify such malware initially.
So we have started developing this feature using which you can ensure that the core WordPress files are clean always. We use the wp-cli tool to check the file hash and replace the files which do not match the original source. It is an automated process and we will send an email alert if any such incidents happen. You can control this option from Settings >> Additional Settings.