Secure websites in Webmin/Virtualmin, Webmin antivirus/antimalware
Secure Webmin/Virtualmin Hosting
Nowadays it is very challenging to keep the websites on your server safe and secure. You can always expect an attack or attempt to compromise your website by attackers, especially towards popular CMS like WordPress. So it is laborious for every web host or server owner to keep updated and defend against such attacks and keep your websites safe.
How cPGuard can help you to secure websites on your Webmin/Virtualmin server?
All the modules in the cPGuard Security Suite work side by side to protect your websites from attacks. It secures your server in various layers, blocks invasion attempts, reduces server load and overhead, and helps to drastically reduce your admin hours dealing with attacks and compromised websites. Given below are some of the cPGuard modules that protect your server
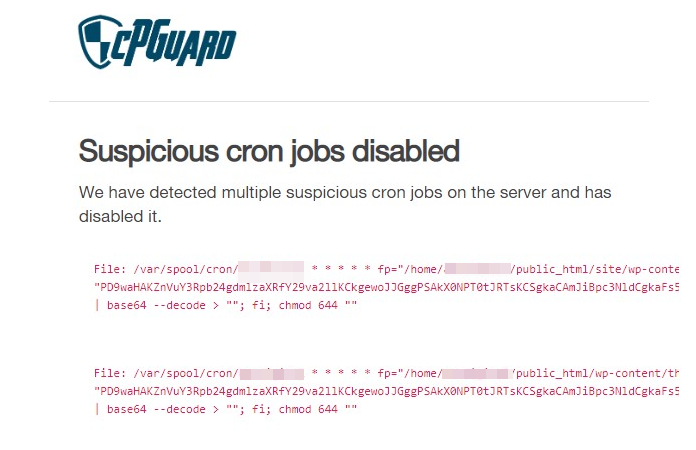
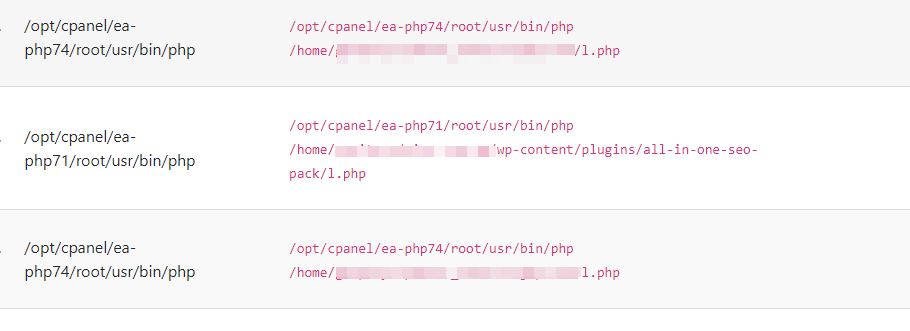
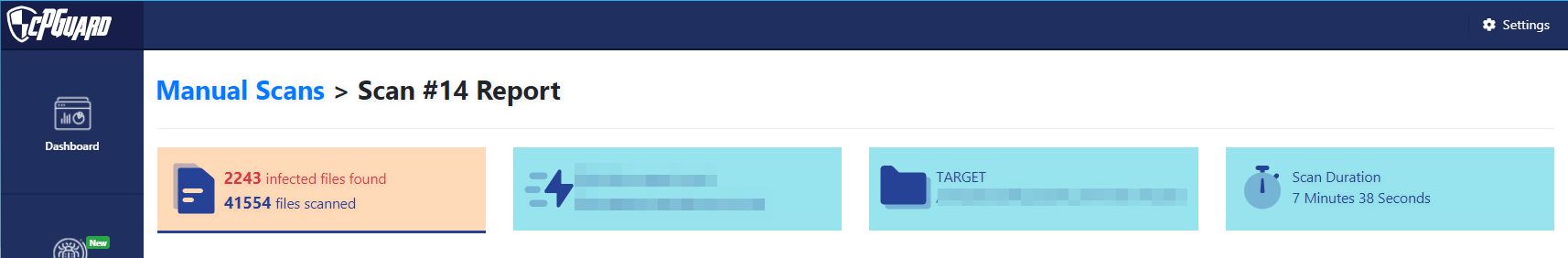
- File Scanner – This module will act as an antivirus/antimalware for websites hosted in Webmin/Virtualmin. Integrated with its cleanup module, this will help to detect and wipe malicious file uploads and injections to your websites
- Web Application Firewall – cPGuards ModSecurity Web Application Firewall rules will stop all generic web attacks against your websites before they even begin. The commercial WAF rules by Malware.Expert protects your Webmin/Virtualmin client websites by effectively blocking generic web attacks, specific web attacks, and bot attacks and more.
- Distributed system firewall – The IPDB distributed system firewall for Webmin/Virtualmin can block traffic from known and active source IPs. This firewall for Webmin/Virtualmin is very much effective to block many attacks even before they reach your application server and thereby reduce your server overhead as well.
- Reputation monitoring – The reputation monitoring module will help to keep an eye on the status of your IP address and domains and alert you if they are listed on blacklists.
There are many other functionalities integrated within cPGuard to help you run your server securely and cleanly. Please read more about the features list at https://opsshield.com/standalone.html
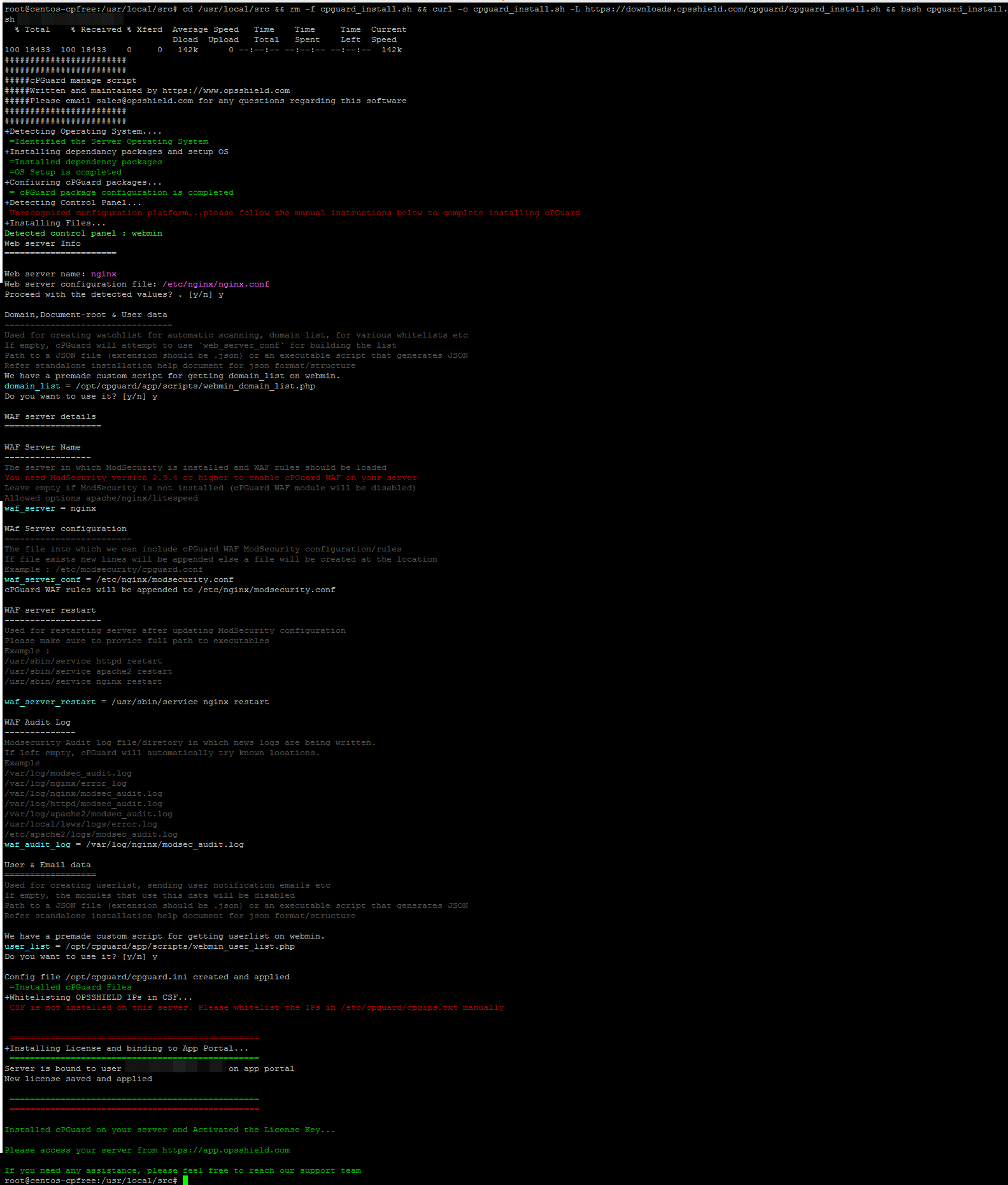
If you wish to secure your Webmin/Virtualmin server, please follow the installation instructions. Installation is pretty simple and we have pre-built templates to support Webmin/Virtualmin servers.
Given below is cPGuard installation sample steps on a Webmin/Virtualmin server.