cPGuard Elevates Webuzo Security with New User-Level Plugin Integration
We are thrilled to announce a significant enhancement to the cPGuard ecosystem: the immediate availability of a user-level plugin for the Webuzo control panel.
In our latest release, we have bridged the gap between server-side security and end-user control. This elevated integration empowers hosting providers using Webuzo to offer premium, self-service security tools directly to their customers, fostering a safer and more transparent hosting environment.
Empowering the End-User
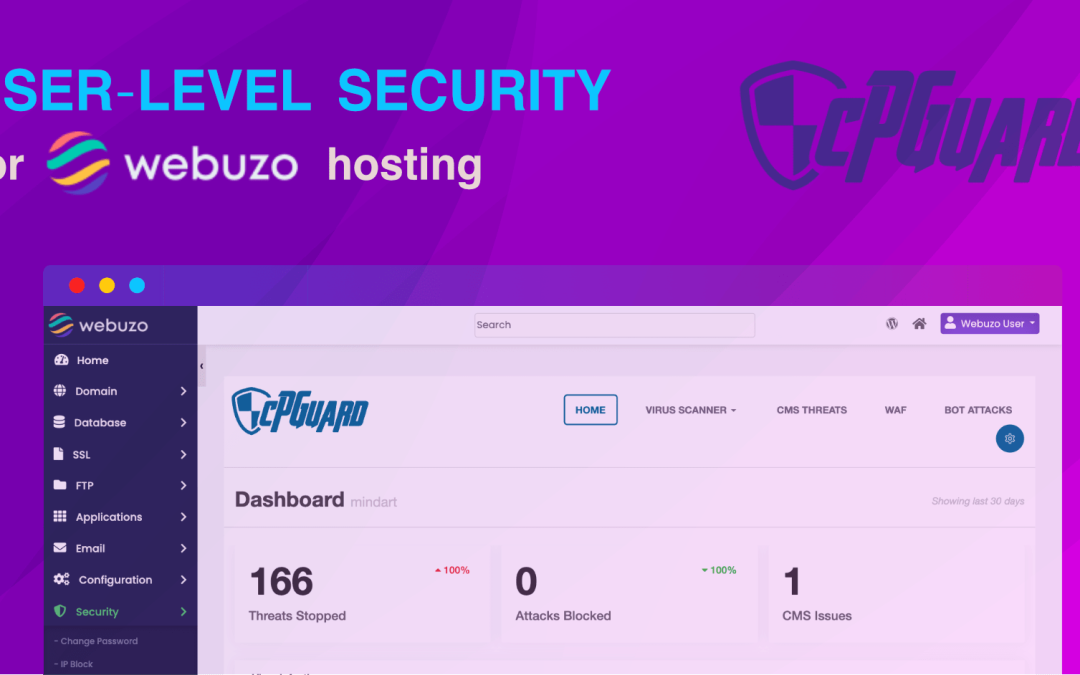
Security is no longer just the administrator’s responsibility; it is a collaborative effort. With this new integration, Webuzo users gain full visibility into their account’s security status.
Key capabilities now available to end-users include:
Detailed Malware Visibility: Users can view specific malware files detected within their account.
On-Demand Scanning: Users can initiate manual file scans instantly, ensuring peace of mind after site updates or uploads.
Real-Time Analytics: Access to comprehensive statistics regarding web attacks targeting their specific websites.
We believe this deeper integration is a game-changer for hosting providers. It allows you to deliver premium security tools that build trust with every client while reducing the support volume related to security queries.
A Quick Preface: What is cPGuard?
For those new to our platform, cPGuard is an all-in-one automated security suite specifically engineered for Linux web hosting servers. It acts as far more than a simple firewall; it provides a multi-layered defense system designed to catch threats that traditional antivirus software often misses.
Our architecture is built on robust pillars of protection:
Smart Malware Scanner: Detects and remediates threats automatically.
Web Application Firewall (WAF): Blocks exploits before they reach applications.
Proactive Attack Blocking (IPDB): A distributed firewall module that leverages global threat intelligence.
CMS Toolkit: Features auto-patching to secure WordPress and other CMS installations proactively.
Why cPGuard is the Strategic Choice
Choosing cPGuard is a strategic decision for server administrators who demand high-level security without the “performance tax” often associated with heavy security suites.
Here is why cPGuard stands out:
Superior Resource Efficiency: Designed to be lightweight, ensuring your server resources are dedicated to serving websites, not running security scans.
Surgical Malware Cleanup: Our intelligent engine cleans malicious injections from core files rather than simply deleting the file, keeping sites online and functional.
Collective IP Intelligence (IPDB): Our distributed firewall module instantly blocks abusive IPs detected anywhere in our global network.
Reduced Management Overhead: Automated tools and a unified dashboard make managing security across multiple servers effortless.
Get Started
Ready to upgrade your Webuzo server’s security posture? The new integration is available now.