cPGuard’s Latest Features: Enhanced Protection Against DoS Attacks and AI Bot Crawling
New Features in cPGuard
In the ever-evolving world of web security, staying ahead of cyber threats is critical. cPGuard, a robust security solution, has introduced new features to its IPDB (IP Database) module, designed to block denial-of-service (DoS) attacks and prevent unwanted crawling by AI bots. These upgrades not only enhance the security of web services but also address some of the most pressing issues faced by website owners today.
1. DoS Mitigation for Web Services
A Denial-of-Service (DoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. The goal is to make the website or service unavailable to legitimate users by exhausting the resources of the targeted system.
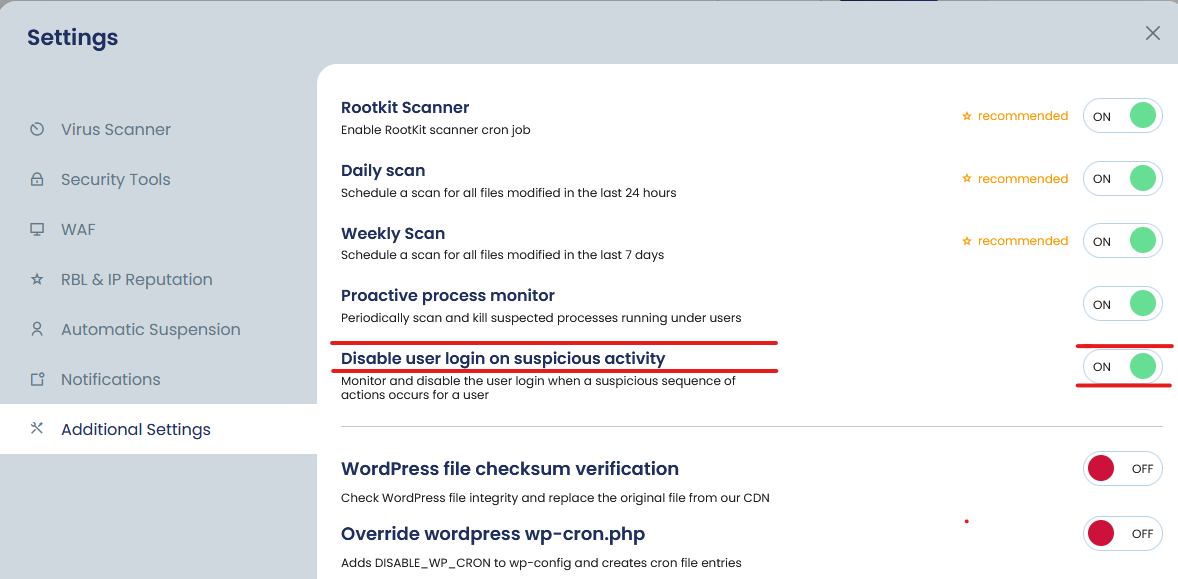
Traditionally, DoS attacks come from a single IP address that bombards a server with an overwhelming number of requests. To combat this, the new feature in cPGuard monitors traffic patterns and can detect when a single IP address begins sending an unusual volume of requests in a short period of time. When this occurs, the system triggers an alert and temporarily blocks the offending IP. This strategy allows the system to recover quickly from the attack without affecting the service for legitimate users.
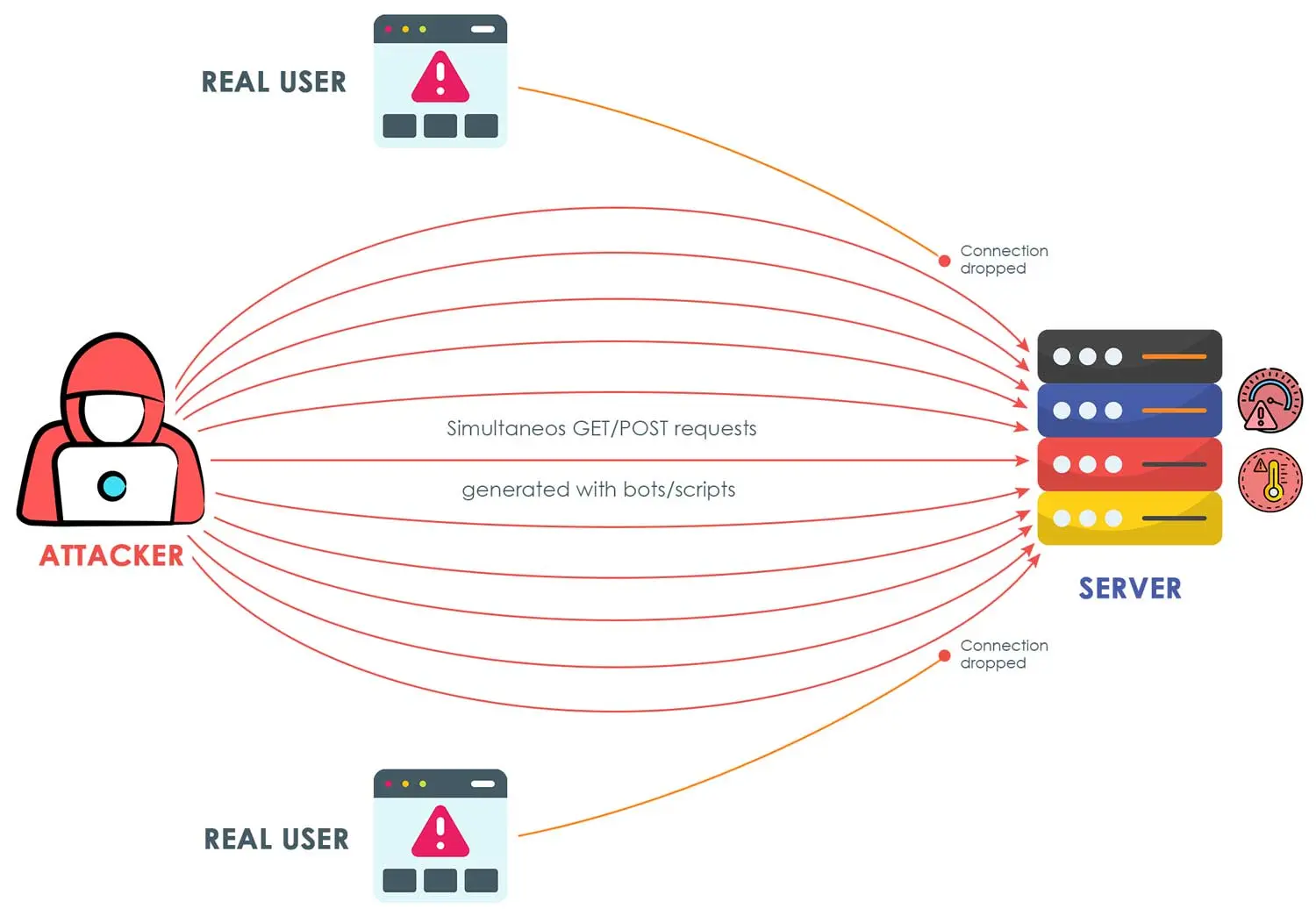
One of the key benefits of this system is its reliance on centrally trained data to avoid mistakenly blocking legitimate traffic from proxies, CDNs, or major search engines. This ensures the DoS mitigation tool works effectively without disrupting vital services.
A customer recently shared feedback highlighting the success of this feature, explaining how it helped their server recover from a persistent DoS attack.
The blocking is working, I see blocking due to DoS in the LOG. The server no longer suffers from instability. Your Dos system is working perfectly. This protection that you implemented deserves to be highlighted and publicized. I have already tested Bitninja, CPFence, but only cPGuard with this new protection is able to efficiently block these Dos attacks.
2. Blocking AI Bots from Crawling Websites
AI bots, while useful in some contexts, can become a nuisance when they aggressively scrape data from websites. These bots are used by various AI-powered tools and search engines to collect data, but their activity can cause a number of problems, including excessive resource usage and potential security risks. Some bots may even gather information about vulnerabilities on your site or scrape valuable content.
Depending on the type of website you operate, you may want to prevent these bots from accessing your site. With the latest cPGuard update, users have two main ways to block unwanted AI bots:
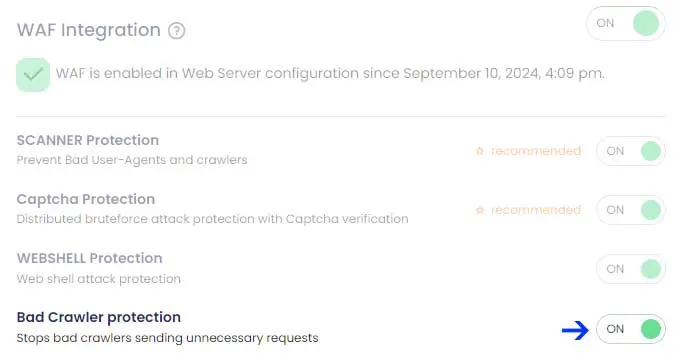
Using Web Application Firewall (WAF): Users can enable “Crawler Rules” within the WAF settings. This will block many well-known AI bots as well as rogue user agents. cPGuard constantly updates its list of bots based on new reports, ensuring comprehensive protection against these automated crawlers.
Using IPDB: The IPDB feature allows users to block AI bot IPs more effectively. cPGuard monitors bot traffic and maintains a dynamic list of over 40,000 IP addresses associated with AI bots. This list is regularly updated to keep up with new threats, giving users peace of mind that their websites are protected from unwanted scraping.
Use the following command to enable
cpgcli ipdb --block-ai-bots enableLooking Ahead: cPGuard’s Future Enhancements
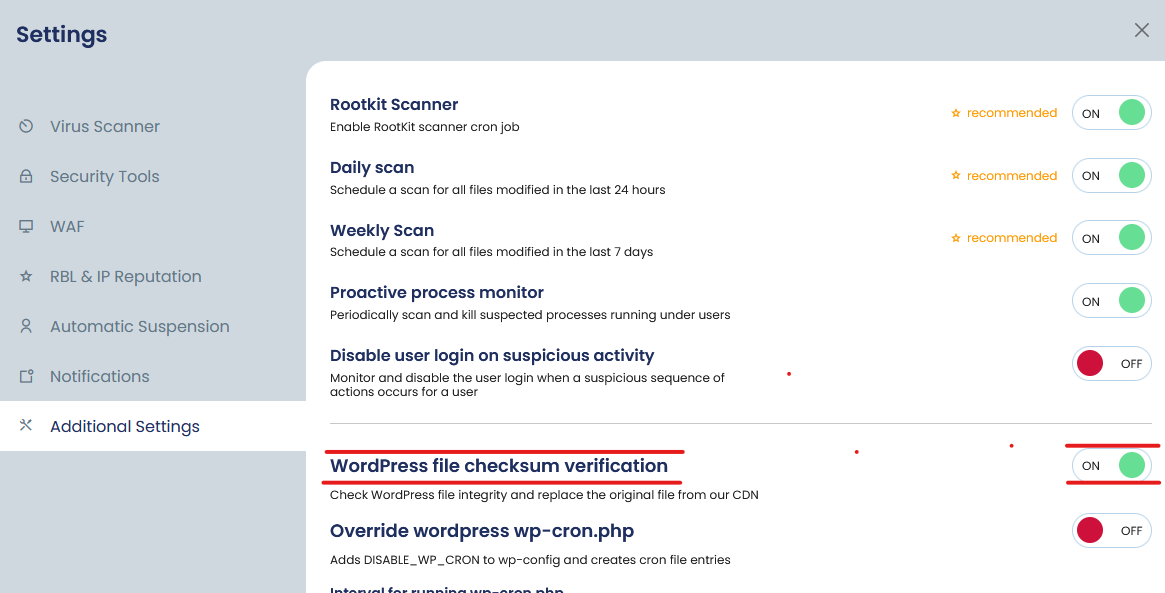
Our team is dedicated to continuously improving the software based on customer feedback and technological advancements. In 2024, We plan to introduce an in-house AI engine to power our malware scanner, along with a database scanning feature specifically tailored for WordPress websites. This upcoming release is expected to provide even more value to users, maintaining cPGuard’s focus on offering effective solutions without over-promising features like “0% false positives” or full DDoS protection.
The primary goal of cPGuard is to offer real, actionable security features at an affordable price, ensuring that customers get exactly what they need to protect their websites without unnecessary extras.
With these new features, cPGuard strives to be the go-to solution for website and server owners, minimizing server admin time by offering simple, effective answers to all common web security needs. From blocking unwanted bots to mitigating DoS attacks, cPGuard’s latest update provides an efficient, comprehensive layer of protection, making web security easier to manage for everyone.