Introducing Enhanced WordPress Management in cPGuard: Simplify Security and Updates
Managing multiple WordPress installations on a server has long been a challenging task for administrators. Each installation comes with its own set of themes, plugins, and potential security vulnerabilities, making it difficult to keep everything up-to-date and secure. This is especially problematic in shared hosting environments where individual users may be unaware of or unconcerned with security implications, exacerbating the overall risk.
We have recently improved the CMS management interface with a special focus on WordPress, the most popular CMS, making it more streamlined, efficient, and secure than ever before to manage WordPress installations on your server.
Centralized Control Over WordPress Installations
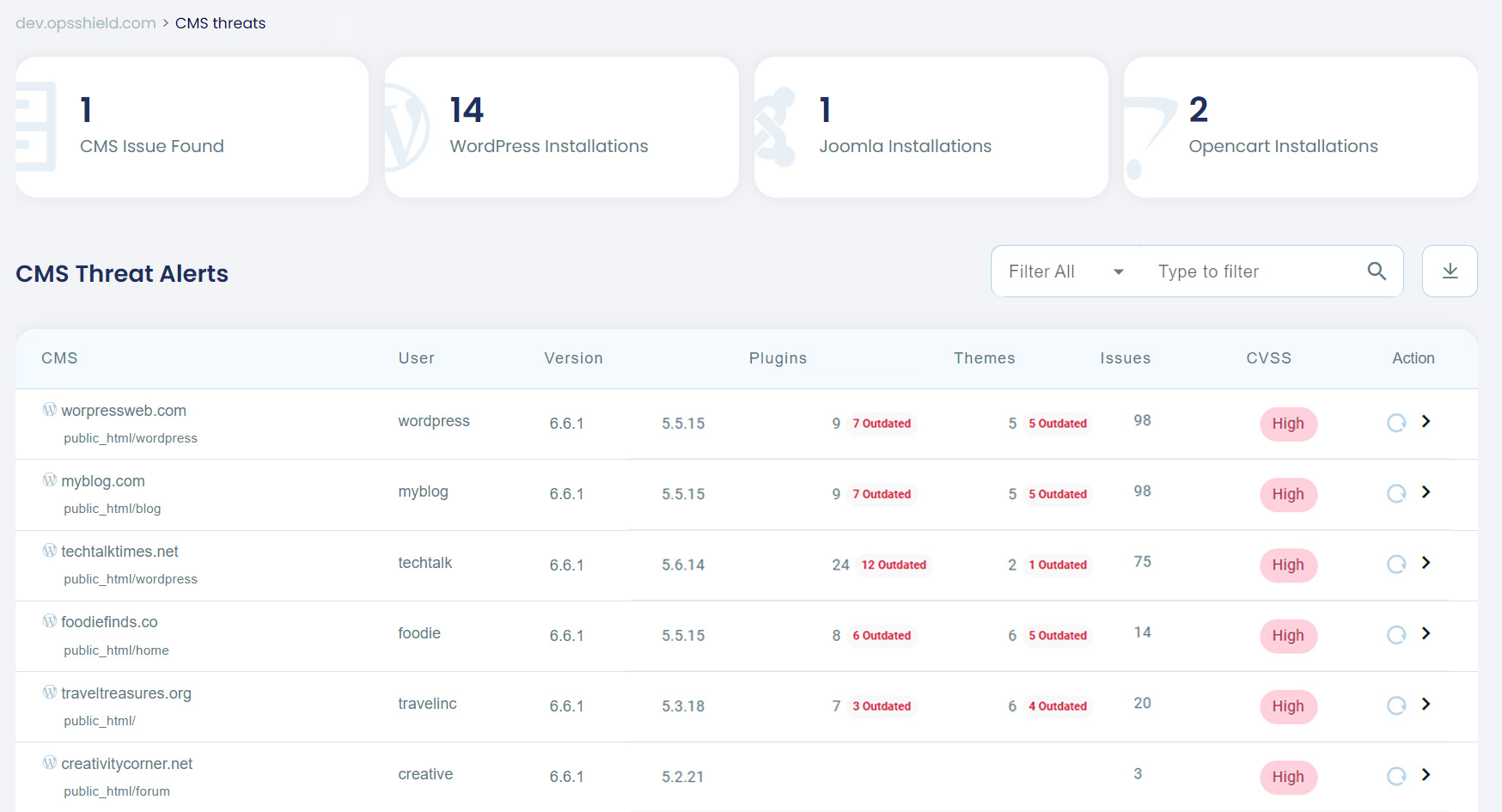
The improved CMS Management feature in cPGuard now provides a centralized interface that lists all the WordPress installations on your server. No more hunting down individual WordPress installations of each user. Now, you can manage everything from a single, intuitive interface.
Key Features:
- Comprehensive Overview: Get a clear picture of all your WordPress installations, including their location, domain, version, details of installed plugins and theme and more.
- Vulnerability Alerts: Stay informed about reported CVEs for the installed version of WordPress core, themes, and plugins.
- Update Status: See which WordPress installations, themes, and plugins require updates and manually update them.
- Automated Updates: Force automatic updates for WordPress installations that meet set criteria, such as CVE score and days since an update was released.
Version Management and Updates
Stay on top of updates for your WordPress core, themes, and plugins. Our system provides clear notifications for available updates, ensuring you’re always aware of potential improvements and security patches. The dashboard provides real-time information on:
- Available Updates: Quickly see if there’s a newer version of WordPress available for each installation. Staying updated ensures you have the latest security patches and features.
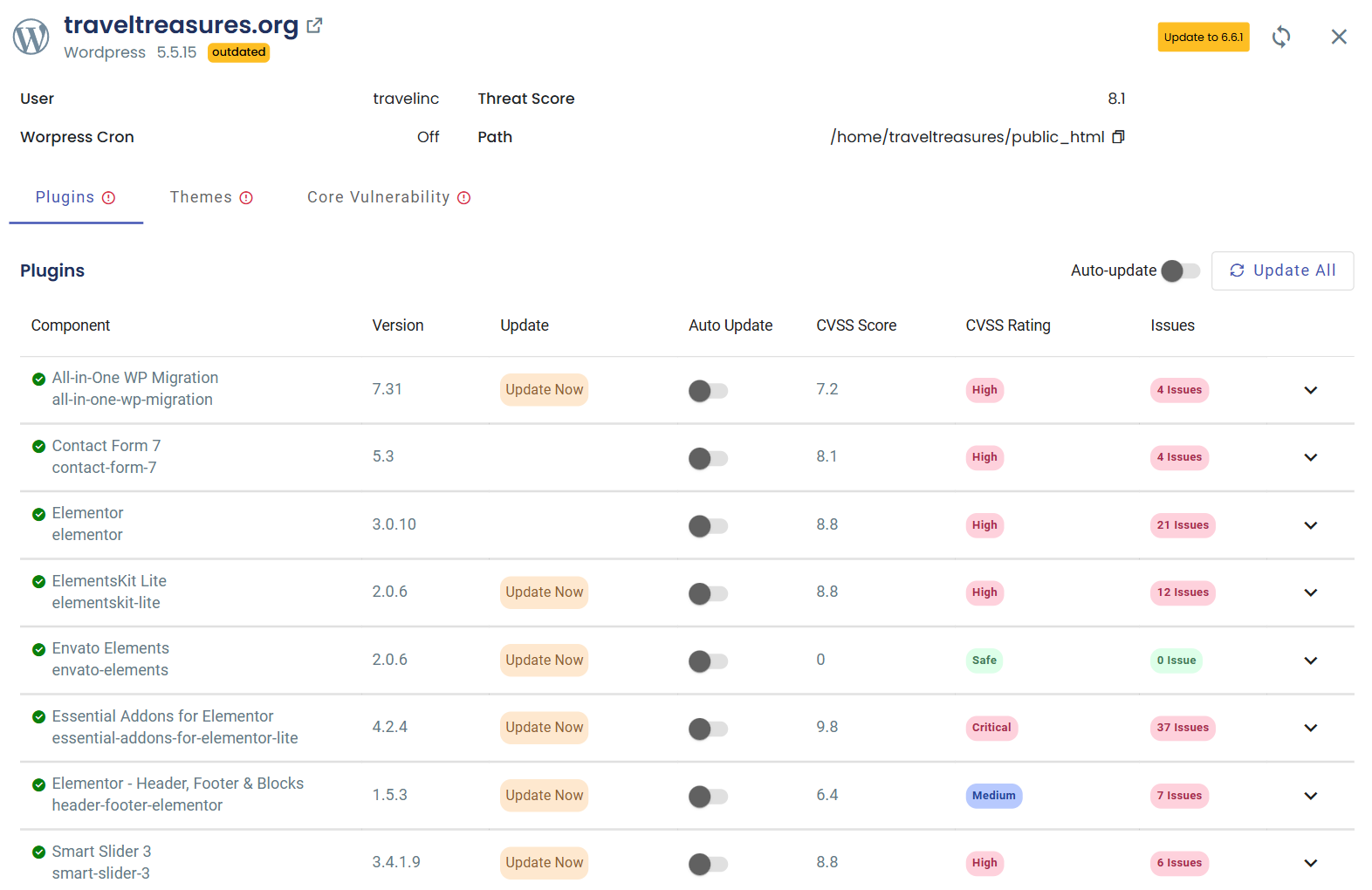
- Plugin and Theme updates: View all installed plugins and themes, their current versions, and whether updates are available.
- Performing updates: We offer convenient options for manually updating your WordPress core, themes, and plugins, or you can set up automatic updates to ensure your website is always protected.
Shared server administrators can use this report to notify or force end users to update their vulnerable WordPress installations and prevent their accounts from being attacked or compromising the server. These features make it easy to monitor the security status of your WordPress sites and ensure they are always running the safest and most stable versions.
Vulnerability Alerts
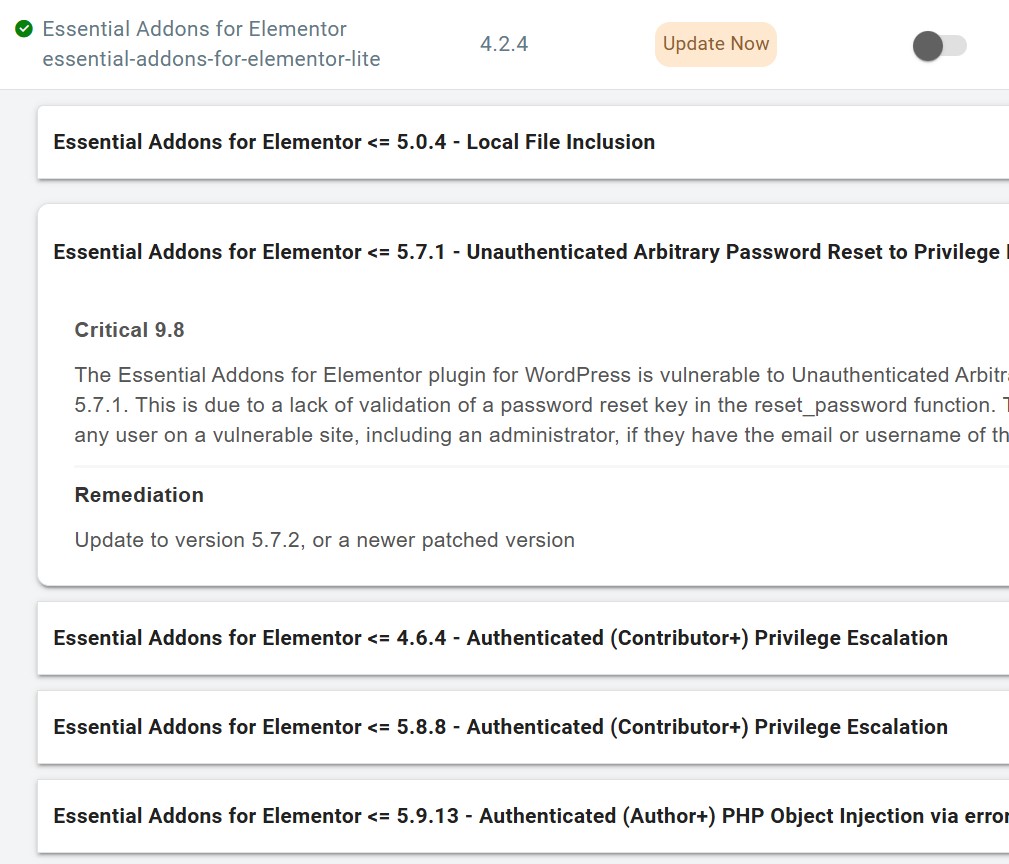
cPGuard keeps a watchful eye on your WordPress core, plugins, and themes, frequently scanning for known vulnerabilities. When it finds a match with a CVE (Common Vulnerabilities and Exposures) report, it alerts you immediately. You can see exactly which version of your WordPress, plugin, or theme is affected, how severe the vulnerability is and provide available remedies. This visual representation allows you to quickly identify and address security risks, ensuring that you can take immediate action to update or patch vulnerable elements.
Shared server administrators can use this report to notify or force end users to update their vulnerable WordPress installations and prevent their accounts from being attacked or compromising the server. These features make it easy to monitor the security status of your WordPress sites and ensure they are always running the safest and most stable versions.
Notifications for Shared Hosting Users
In shared hosting environments, managing the security of multiple WordPress installations can be challenging. To streamline this process, When updates or vulnerabilities are detected for any WordPress installation on your server, we send automated email alerts directly to the shared account users. This ensures that your customers are informed about potential security risks and can take appropriate action promptly.
This eliminates the need for server administrators to manually find WordPress installations and notify users individually. Instead, users receive timely (customisable) alerts directly in their inbox, prompting them to update their WordPress core, themes, and plugins, or take action if vulnerabilities are detected. This automated notification system enhances the overall security of the server, keeping both the administrators and users informed and reducing the risk of outdated or vulnerable installations.
Automated forced updates
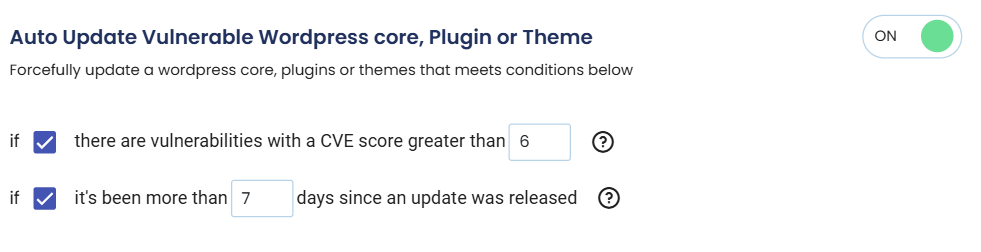
For administrators who prefer a more automated approach, cPGuard’s WordPress Management feature includes an Auto-Update option. This powerful tool allows you to set criteria for automatically updating WordPress installations that meet set criteria like:
- Vulnerability Response: Automatically update WordPress if there are reported vulnerabilities above a certain score (based on severity or reported vulnerabilities).
- Update Timing: Define how many days after a WordPress update is released that it should be automatically applied to your installations.
These custom settings help shared server administrators to intervene and automatically force update a WordPress installation if the end-user does not promptly update the sites on their own. With these automation options, you can ensure your WordPress sites are always up-to-date without constant manual intervention, giving you peace of mind that your sites are secure.
Why This Feature Matters
WordPress powers over 40% of the web, making it a prime target for hackers and cyber threats. Keeping WordPress installations and their associated plugins and themes up-to-date is critical for maintaining security and performance. cPGuard’s new WordPress Management feature takes the hassle out of this process, offering a comprehensive, easy-to-use toolset that simplifies the management of multiple WordPress sites.
By providing a centralized dashboard, real-time updates, vulnerability alerts, and automation options, cPGuard empowers you to maintain a secure and up-to-date WordPress environment with minimal effort. This new feature is a must-have for any server administrator looking to protect their WordPress sites from the ever-evolving landscape of online threats.