It is a well-known fact that WordPress is one of the web applications that get the majority of web attacks when installed on a domain. In addition to the conventional attack vectors, there are plenty of other attack methods that are being used to attack WordPress website and applications. So all WordPress website owners should protect their websites using an additional security layer to protect their website from common attacks like brute-force, SQL injection, Cross-site attacks, etc and other unconventional types of attacks.
Nulled Plugins and Themes
When we talk about other types of attacks, one of the most tricky types is the installation of “Nulled Plugins and Themes”. We recently had a customer, who came to us regarding clean up of his websites which had nulled plugins installed. The funny fact is that the client knew that they were nulled but decided to install them as they are free but never knew they will open up a backdoor to his websites.
So how it can damage your websites?
The severity of the damage that can be done is based on the source of these nulled plugin/theme. In the specific case that we are taking as an example here, the plugins where downloaded from thewordpressclub [.] org and the websites faced the following issues.
- Repeated JS injections into the database which resulted in redirects to malicious websites upon website visit.
- Added junk records to the wp_options table for the backdoor
- The admin user password kept resetting without the knowledge of website owner
- Unwanted posts created under the websites
and many more…..
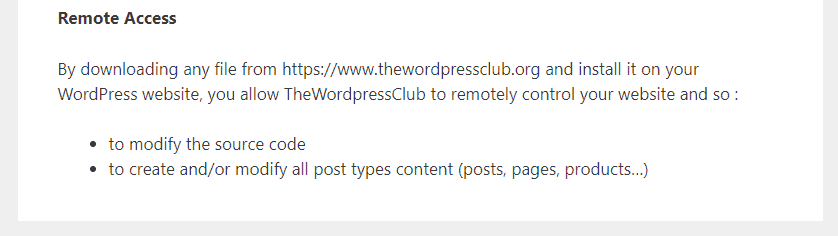
Interestingly, the terms and conditions at thewordpressclub [.] org has a section Remote Access stating that by downloading and installing installing these plugins/themes you are allowing TheWordpressClub to remotely control your website
What kind of injection were added to the nulled plugins?
We have noted the following files added to the plugin packages, which contained the core code.
rms-script-ini.php
rms-script-mu-plugin.phpFor example, following are some sample paths in actual plugin installations
wp-content/mu-plugins/rms_unique_wp_mu_pl_flnm.php
wp-content/plugins/YITH Product Description In Loop For WooCommerce Premium 1.0.6/rms-script-mu-plugin.php
wp-content/plugins/YITH Product Description In Loop For WooCommerce Premium 1.0.6/plugin-fw/templates/panel/rms-script-mu-plugin.php
wp-content/plugins/YITH Product Description In Loop For WooCommerce Premium 1.0.6/plugin-fw/templates/panel/rms-script-ini.php
wp-content/plugins/YITH Product Description In Loop For WooCommerce Premium 1.0.6/rms-script-ini.php
wp-content/plugins/WP Smush Pro 3.6.3/rms-script-mu-plugin.php
wp-content/plugins/WP Smush Pro 3.6.3/core/external/dash-notice/rms-script-mu-plugin.php
wp-content/plugins/WP Smush Pro 3.6.3/core/external/dash-notice/rms-script-ini.php
wp-content/plugins/WP Smush Pro 3.6.3/rms-script-ini.phpIn addition to that, they have added the following lines to other files to use the malicious function and active the remote handler.
require_once('rms-script-ini.php');
rms_remote_manager_init(__FILE__, 'rms-script-mu-plugin.php', false, false);How to get rid of such issues?
The answer is pretty straightforward; do not install plugins/themes from non-trusted sources. If you want to install a plugin/theme, you should use WordPress official repository to search and install or use the official website of the provider to download the package. If you try to enjoy the premium features of any paid solution for free using such shortcuts, you will end up with serious trouble including your data loss.
Though cPGuard can detect and clean the majority of these malicious injections, we strongly recommended to stay away from such plugin providers and use only the genuine software

